Safeguarding Compromised Cell Phones From Pegasus Spyware
KEY TAKEAWAYS
Pegasus Spyware has emerged as a dangerous threat because it requires one errant click on a message or email to turn the whole phone over to a remote bad guy. For instance, the phone stays under hostile control forever. In some cases, applications like Pegasus can be installed even if the user never clicks the “trap” message. Given the ability for phones to communicate their location, surveillance can be set to begin only when a phone enters certain target locations such as secure government buildings, major corporations, entertainment studios, and more.
How can organizations and government agencies protect compromised cell phones from the Pegasus Spyware? Enter Bastille Networks.
Bastille Networks, the leader in enterprise threat detection through software-defined radio, recently announced the company’s Bastille Enterprise provides corporations and agencies the ability to discover, locate, and mitigate radio-borne threats from the Pegasus Spyware. Pegasus Spyware demonstrates that a remote attacker can activate the camera and microphone on any cell phone to exfiltrate conversations or video meetings. NSO Group, the Israeli maker of Pegasus, claims that their system is designed never to attack a phone with a U.S. phone number. However, findings suggest that Pegasus has exploited phones on U.S. soil which had overseas numbers.

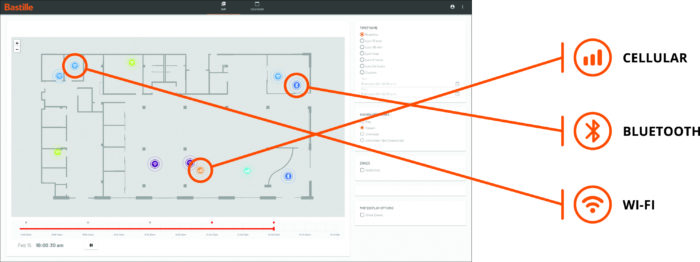
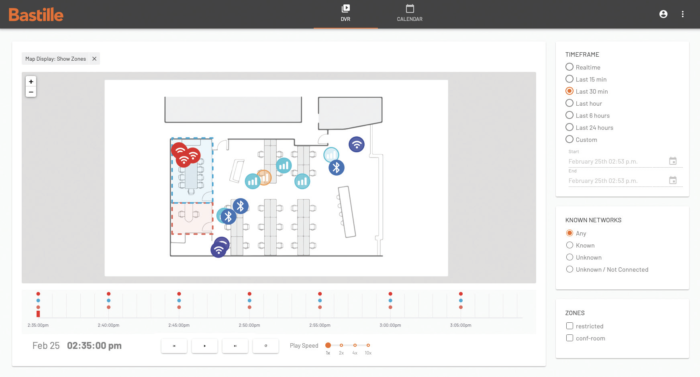
Bastille detects and locates unauthorized cellphones to produce an accurate dots-on-the-floor plan of facilities, offering security teams situational awareness with features such as geofencing, hotspot detection, SIEMS integration, and DVR forensics. Below are use case examples from enterprises, defense, and civilian agencies:
- Enforce device policy: Detect cell phones in breach of cell phone policies for sensitive or no-cell phone areas.
- Scan tent sites, buildings, and remote offices: Scan a room or building to understand the presence and location of all emitters/transmitters and building systems.
- Secure meeting areas: Detect transmitting electronic devices in secure meeting areas.
“Bastille has been doing RF and Cellular Intrusion Detection and research for the government for years and the Pegasus Projects reporting this week should put all enterprises on alert. Millions of vulnerable smartphones enter workplaces daily. A hacked smartphone can be used as a portal into an enterprise’s network, putting the organization’s sensitive and critical data at risk of being breached. It is imperative to have security protocols in place to manage the secure use of smartphones in the workplace. If security teams didn’t think smartphones in the facility were an important threat in July, they certainly should think they are an important threat now,” Risley added.
The U.S. government is highly concerned about RF espionage because nation-state actors such as China, North Korea, Russia, and Israel are very savvy at employing RF techniques to breach network security. The government has accepted the threat of RF espionage and because of this, government facilities with valuable secrets have policies to exclude RF devices such as cell phones to keep the threats at bay. While some government and commercial buildings have secure areas where no cell phones or other RF-emitting devices are allowed, detecting and locating radio-enabled devices is largely based on the honor system or one-time scans for devices. Unfortunately, nation-states and other bad actors do not follow the honor system and one-time scans are just that: one time and cannot monitor 24×7.
Bastille equips customers to locate and detect all the cell phones in their facilities whether or not those phones have Wi-Fi or Bluetooth turned on. Notably, Bastille is the only civilian product that can locate cell phones indoors by detecting cellular signals. Bastille ensures that there are no non-authorized cell phones, therefore no infected phones in sensitive areas. Bastille is trusted by military, government and Fortune 500 customers to instantly detect, locate and alert on the presence of rogue cell phones and other radio frequency (RF) based devices anywhere within a facility.